WAN through Hotspot 2.0/Passpoint
Introduction
- Hotspot 2.0/Passpoint uses WPA2/3 Enterprise security to authenticate users.
- Not all WiFi devices support WPA2 Enterprise security.
- WPA2 Enterprise security typically involves a username and password or certificates.
- Most printers, gaming consoles or IoT equipment only support WPA Personal.
- Should the need arise for them to also join an enterprise network we developed a central managed solution that can act as a bridge.
- This page provides a more detailed explanation of our solution.
The Eduroam Travel Router
 Consider the following practical example.
Consider the following practical example.
- Meet Tim.
- Tim is the network administrator of a big university somewhere in Europe.
- The university participates in Eduroam.
- The university has a couple of scientists working on specialized equipment that only has network access through an Ethernet port.
- Each of these scientists will travel to other universities over the next few months to give demonstrations and talks.
- These universities also participate in Eduroam.
- Tim will now configure an Eduroam Travel Router on APdesk for each of these scientists.
- This will allow them to connect their specialized equipment to the router while the router uses the Hotspot 2.0 connection as the uplink.
- Many travel routers allow you to have a WPA2 Enterprise uplink.
- We don't know of any centrally managed travel routers that supports Hotspot 2.0 uplinks besides the ones managed by APdesk and MESHdesk.
Acknowledgement
- We would like to acknowledge and express our gratitude to the individuals who contributed to and provided valuable information and projects that served as references for developing this enhancement to MESHdesk and APdesk.
WPA-ENTERPRISE/HS2.0 UPLINKS
- RADIUSdesk now have a WPA-ENTERPRISE/HS2.0 UPLINKS applet that makes the management of WPA-Enterprise and Hotspot 2.0 uplinks a breeze.
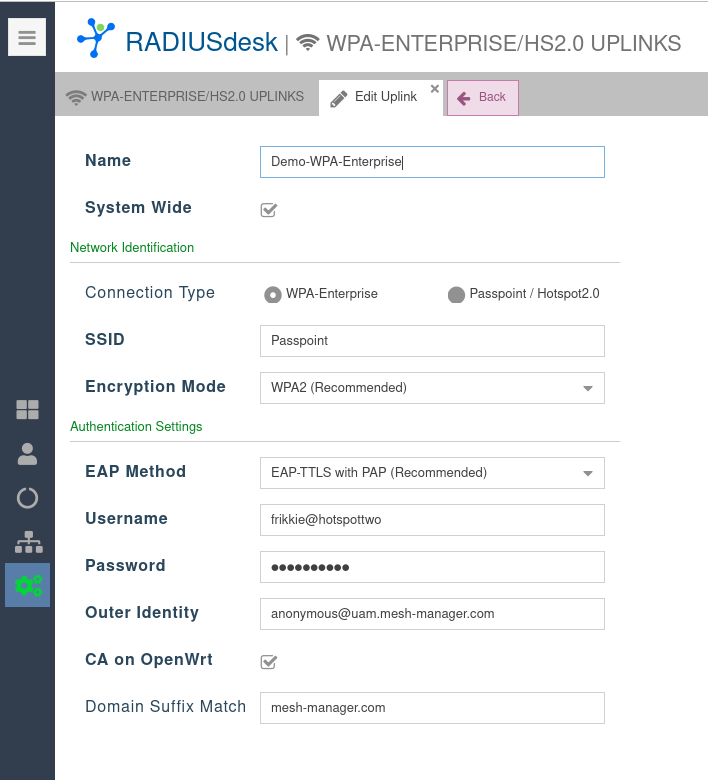
WPA-Enterprise Uplink
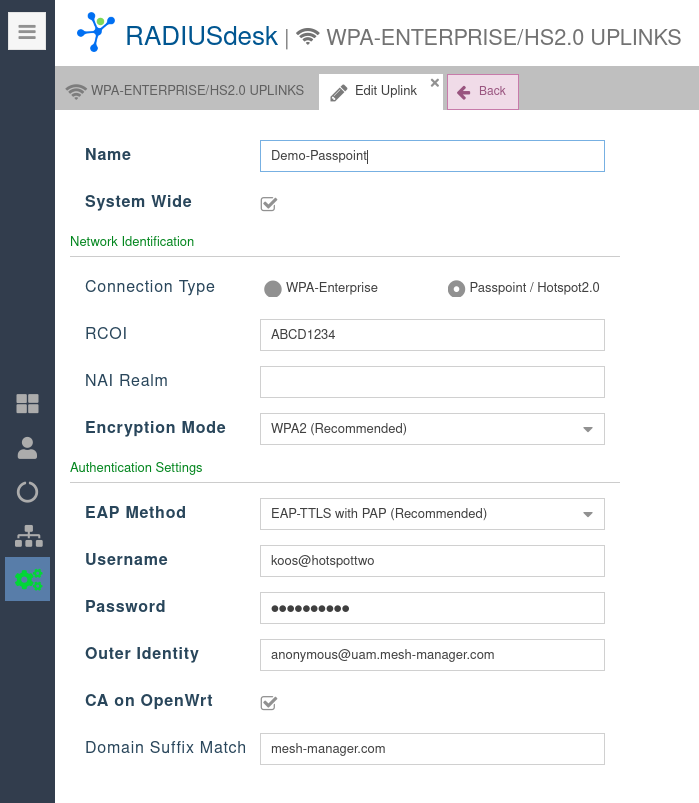
Passpoint / Hotspot 2.0 Uplink
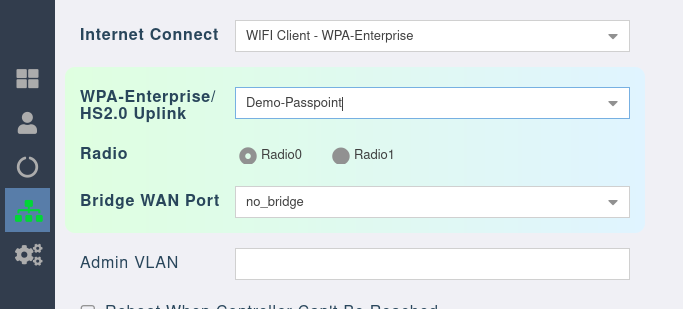
Assigning the Uplink
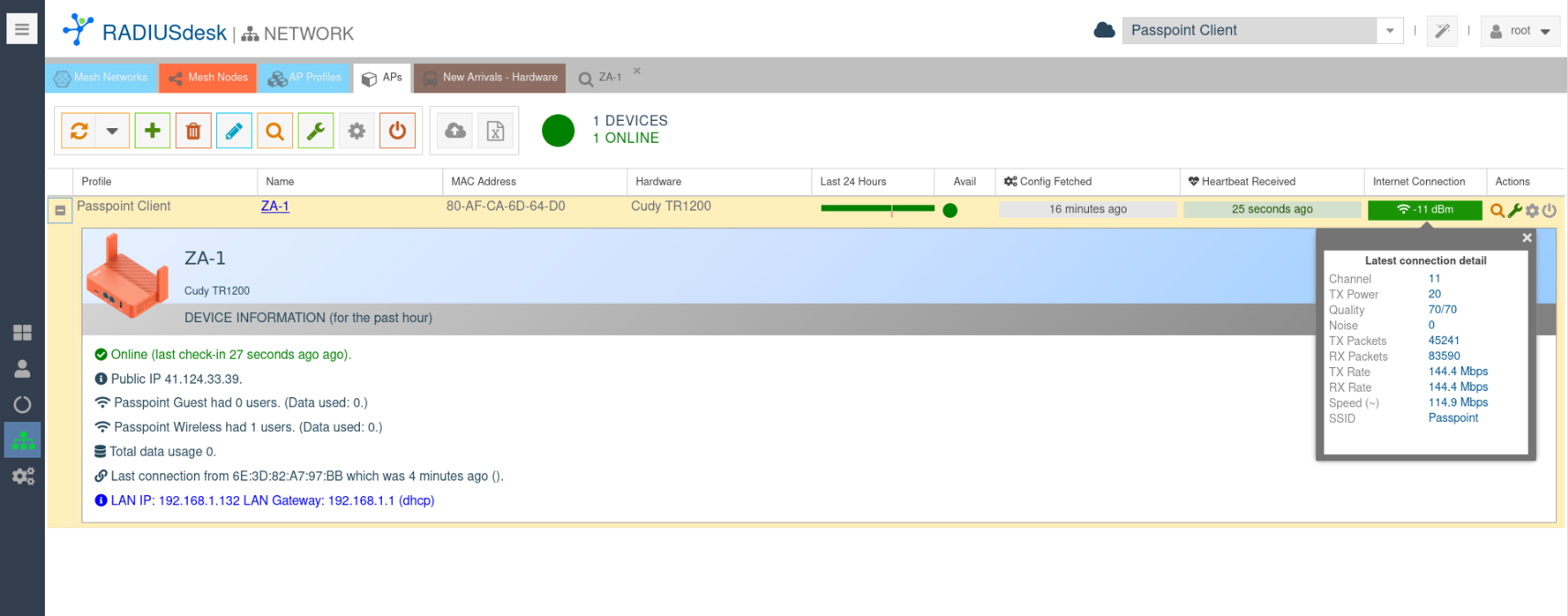
Connected
Technical detail
- When you select a specific uplink, the detail for that uplink will be assigned to the AP or mesh node when it fetched its settings.
- The MESHdesk firmware contains a modified /lib/netifd/hostapd.sh file that allows the AP to be able to connect to Hotspot 2.0 networks.
- One very important item to remember if you are security conscious it the Domain Suffix Match. This protects you against Evil Twin attacks.
- Lets look at some sample configs and feedback from the logread command.
Building the firmware
- You can follow the firmware building instructions as stipulated for the normal MESHdesk firmware on OpenWrt.
- There are just two deviations:
- Use the wpad-ssl (full) package instead of wpad (full) package under Network → WirelessAPD.
- Under the openwrt/files folder, create the /lib/netifd/ directory.
- Copy the /openwrt-meshdesk/passpoint_client/24.10/hostapd.sh file in there as a drop in replacement. This is so that the access point can run a Hotspot 2.0 / Passpoint uplink.
Passpoint / Hotspot 2.0
- The /etc/config/wireless part
config wifi-iface 'web_by_w' option ifname 'wbw' option disabled '0' option encryption 'wpa2' option identity 'koos@hotspottwo' option mode 'sta' option ca_cert_usesystem '1' option ieee80211w '1' option ssid '_Passpoint' option iw_rcois 'ABCD1234' option device 'radio0' option anonymous_identity 'anonymous@uam.mesh-manager.com' option password 'testing123' option eap_type 'ttls' option iw_enabled '1' option network 'web_by_w' option auth 'PAP'
- hostapd.sh then generates /tmp/run/wpa_supplicant-wbw.conf
country=ZA interworking=1 hs20=1 auto_interworking=1 cred={ roaming_consortiums="ABCD1234" ca_cert="/etc/ssl/certs/ca-certificates.crt" username="koos@hotspottwo" password="testing123" phase2="auth=PAP" eap=TTLS } network={ scan_ssid=1 ssid="_Passpoint" key_mgmt=WPA-EAP WPA-EAP-SHA256 ca_cert="/etc/ssl/certs/ca-certificates.crt" identity="koos@hotspottwo" anonymous_identity="anonymous@uam.mesh-manager.com" password="testing123" phase2="auth=PAP" eap=TTLS proto=RSN ieee80211w=1 beacon_int=100 }
- And here is the output of logread
Fri Jul 4 06:56:22 2025 daemon.notice wpa_supplicant[2163]: wbw: Starting ANQP fetch for 80:af:ca:18:22:48 (HESSID 00:00:00:01:02:03) Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: GAS-QUERY-START addr=80:af:ca:18:22:48 dialog_token=100 freq=2462 Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: GAS-QUERY-DONE addr=80:af:ca:18:22:48 dialog_token=100 freq=2462 status_code=0 result=SUCCESS Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: RX-ANQP 80:af:ca:18:22:48 ANQP Capability list Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: RX-HS20-ANQP 80:af:ca:18:22:48 HS Capability List Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: ANQP-QUERY-DONE addr=80:af:ca:18:22:48 result=SUCCESS Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: ANQP fetch completed Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: INTERWORKING-AP 80:af:ca:18:22:48 type=unknown id=1 priority=0 sp_priority=0 Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: INTERWORKING-SELECTED 80:af:ca:18:22:48 Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: SME: Trying to authenticate with 80:af:ca:18:22:48 (SSID='Passpoint' freq=2462 MHz) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.702035] wbw: authenticate with 80:af:ca:18:22:48 (local address=82:af:ca:6d:64:d0) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.710213] wbw: send auth to 80:af:ca:18:22:48 (try 1/3) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.721862] wbw: authenticated Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: Trying to associate with 80:af:ca:18:22:48 (SSID='Passpoint' freq=2462 MHz) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.749689] wbw: associate with 80:af:ca:18:22:48 (try 1/3) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.779748] wbw: RX AssocResp from 80:af:ca:18:22:48 (capab=0x1431 status=0 aid=1) Fri Jul 4 06:56:23 2025 kern.info kernel: [ 211.787772] wbw: associated Fri Jul 4 06:56:23 2025 daemon.notice netifd: Network device 'wbw' link is up Fri Jul 4 06:56:23 2025 daemon.notice netifd: Interface 'web_by_w' has link connectivity Fri Jul 4 06:56:23 2025 daemon.notice netifd: Interface 'web_by_w' is setting up now Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: Associated with 80:af:ca:18:22:48 Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-STARTED EAP authentication started Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0 Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=4 -> NAK Fri Jul 4 06:56:23 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=21
- As you can see the AP does a GAS query to locate the SSID it needs to connect to.
WPA2 Enterprise
- The /etc/config/wireless part
config wifi-iface 'web_by_w' option ifname 'wbw' option disabled '0' option encryption 'wpa2' option identity 'frikkie@hotspottwo' option mode 'sta' option ca_cert_usesystem '1' option ssid 'Passpoint' option device 'radio0' option anonymous_identity 'anonymous@uam.mesh-manager.com' option password 'testing123' option eap_type 'ttls' option network 'web_by_w' option auth 'PAP'
- hostapd.sh then generates /tmp/run/wpa_supplicant-wbw.conf
country=ZA network={ scan_ssid=1 ssid="Passpoint" key_mgmt=WPA-EAP ca_cert="/etc/ssl/certs/ca-certificates.crt" identity="frikkie@hotspottwo" anonymous_identity="anonymous@uam.mesh-manager.com" password="testing123" phase2="auth=PAP" eap=TTLS proto=RSN beacon_int=100 }
- And here is the output of logread
Fri Jul 4 07:05:56 2025 daemon.notice wpa_supplicant[2163]: wbw: SME: Trying to authenticate with 80:af:ca:18:22:48 (SSID='Passpoint' freq=2462 MHz) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.891059] wbw: authenticate with 80:af:ca:18:22:48 (local address=82:af:ca:6d:64:d0) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.899143] wbw: send auth to 80:af:ca:18:22:48 (try 1/3) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.909477] wbw: authenticated Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: Trying to associate with 80:af:ca:18:22:48 (SSID='Passpoint' freq=2462 MHz) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.940594] wbw: associate with 80:af:ca:18:22:48 (try 1/3) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.952689] wbw: RX AssocResp from 80:af:ca:18:22:48 (capab=0x1431 status=0 aid=1) Fri Jul 4 07:05:57 2025 kern.info kernel: [ 216.960814] wbw: associated Fri Jul 4 07:05:57 2025 daemon.notice netifd: Network device 'wbw' link is up Fri Jul 4 07:05:57 2025 daemon.notice netifd: Interface 'web_by_w' has link connectivity Fri Jul 4 07:05:57 2025 daemon.notice netifd: Interface 'web_by_w' is setting up now Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: Associated with 80:af:ca:18:22:48 Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0 Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-STARTED EAP authentication started Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=4 -> NAK Fri Jul 4 07:05:57 2025 daemon.notice wpa_supplicant[2163]: wbw: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=21