Hotspot 2.0/Passpoint User On-boarding
- One of the critical factors of a Hotspot2.0 deployment is the ease to onboard users.
- The initial Hotspot 2.0 standard included Online Signup functionality (OSU).
- This included a Signup Server which used XML and SOAP to communicate between it and the client's WiFi supplicant.
- If you think Hotspot 2.0 never took off, the OSU functionality ultimately failed even more to gain traction.
- The more recent revisions of Hotspot 2.0 have thus removed the OSU feature all together.
Simplicity is king
- A simpler approach is the way OpenRoaming does things via a portal. (https://www.openroamingconnect.org/)
- User registers on the portal.
- During registration, the system creates a RADIUS user that can be used with WPA2 Enterprise authentication.
- Users can log into the portal where they are given the options to download and install Hotspot 2.0 profiles that are tailor made to a preset Hotspot 2.0 configuration and for a specific operating system.
- Items that can be tweaked are:
- Realms
- NAI Realms
- RCOIs
- Authentication method
- Allowed CA.
Rd-Connect
- We do something similar to the OpenRoaming Portal with Rd-Connect.
- Rd-Connect is a work in progress with extended functionality in mind in MDU deployments that uses a combination of Private PSK and Hotspot 2.0.
- We currently have the following functionality / options
- Choice to install as an mobile app on Android and Apple.
- User registration
- Password management
- Hotspot 2.0 Profile download and install for
- Android
- Apple
- Rd-Connect allows you to specify your own:
- Hotspot 2.0 Domain
- NAI Realms
- RCOIs
- Certificate Authority and allowed FQDN for EAP Certificates
Install Rd-Connect (Server Side)
- Rd-Connect runs on the same server as RADIUSdesk
cd /var/www sudo git clone https://github.com/RADIUSdesk/rd_connect.git cd /var/www/html #For the RD-Connect Mobile UI sudo ln -s ../rd_connect/build/production/RdConnect ./rd_connect
Configure Rd-Connect
- Rd-Connect work as part of a RADIUSdesk deployment and rely on two items in RADIUSdesk to be configured properly in order for it to work as intended.
- Each RADIUS Realm in RADIUSdesk has optional configuration related to Hotspot2.0/Passpoint. You need to configure the Realms → Hotspot2.0/Passpoint settings to match your environment.
- To allow user registration we will latch onto an existing Login Page where the User Registration is already configured.
- Once these two items have been configured we can do the last tweaks on Rd-Connect's config file for everything to work together as a unit.
Realm -> Hotspot2.0/Passpoint
- See the screenshot below as reference.
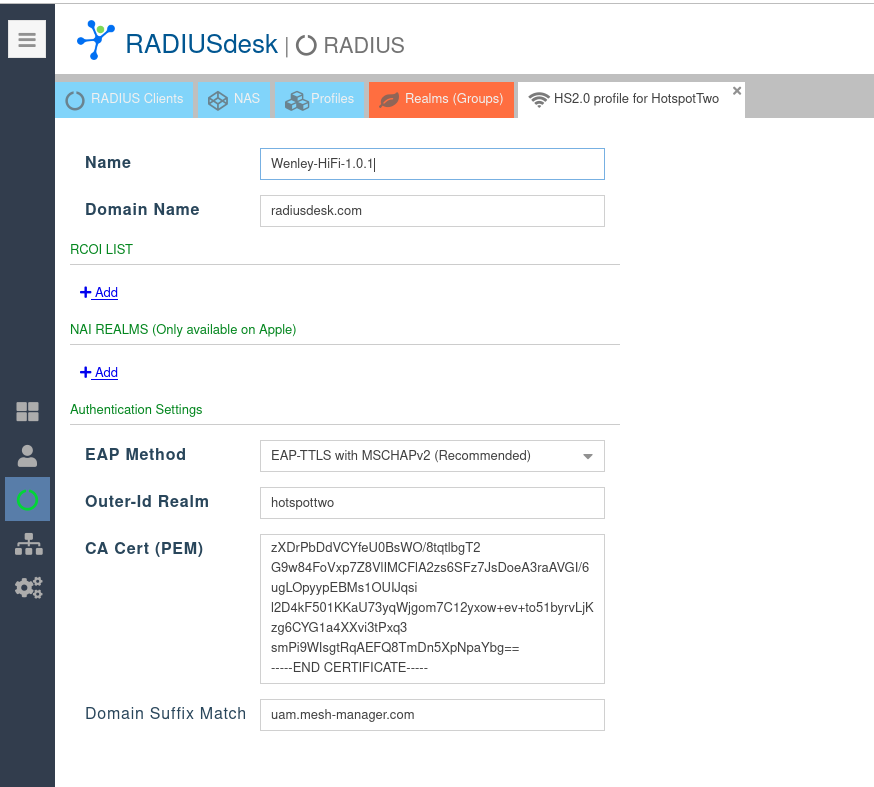
- If you use the FreeRADIUS config that is part of RADIUSdesk, the CA file is as follows:
-----BEGIN CERTIFICATE----- MIIEMjCCAxqgAwIBAgIBATANBgkqhkiG9w0BAQUFADB7MQswCQYDVQQGEwJHQjEb MBkGA1UECAwSR3JlYXRlciBNYW5jaGVzdGVyMRAwDgYDVQQHDAdTYWxmb3JkMRow GAYDVQQKDBFDb21vZG8gQ0EgTGltaXRlZDEhMB8GA1UEAwwYQUFBIENlcnRpZmlj YXRlIFNlcnZpY2VzMB4XDTA0MDEwMTAwMDAwMFoXDTI4MTIzMTIzNTk1OVowezEL MAkGA1UEBhMCR0IxGzAZBgNVBAgMEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4GA1UE BwwHU2FsZm9yZDEaMBgGA1UECgwRQ29tb2RvIENBIExpbWl0ZWQxITAfBgNVBAMM GEFBQSBDZXJ0aWZpY2F0ZSBTZXJ2aWNlczCCASIwDQYJKoZIhvcNAQEBBQADggEP ADCCAQoCggEBAL5AnfRu4ep2hxxNRUSOvkbIgwadwSr+GB+O5AL686tdUIoWMQua BtDFcCLNSS1UY8y2bmhGC1Pqy0wkwLxyTurxFa70VJoSCsN6sjNg4tqJVfMiWPPe 3M/vg4aijJRPn2jymJBGhCfHdr/jzDUsi14HZGWCwEiwqJH5YZ92IFCokcdmtet4 YgNW8IoaE+oxox6gmf049vYnMlhvB/VruPsUK6+3qszWY19zjNoFmag4qMsXeDZR rOme9Hg6jc8P2ULimAyrL58OAd7vn5lJ8S3frHRNG5i1R8XlKdH5kBjHYpy+g8cm ez6KJcfA3Z3mNWgQIJ2P2N7Sw4ScDV7oL8kCAwEAAaOBwDCBvTAdBgNVHQ4EFgQU oBEKIz6W8Qfs4q8p74Klf9AwpLQwDgYDVR0PAQH/BAQDAgEGMA8GA1UdEwEB/wQF MAMBAf8wewYDVR0fBHQwcjA4oDagNIYyaHR0cDovL2NybC5jb21vZG9jYS5jb20v QUFBQ2VydGlmaWNhdGVTZXJ2aWNlcy5jcmwwNqA0oDKGMGh0dHA6Ly9jcmwuY29t b2RvLm5ldC9BQUFDZXJ0aWZpY2F0ZVNlcnZpY2VzLmNybDANBgkqhkiG9w0BAQUF AAOCAQEACFb8AvCb6P+k+tZ7xkSAzk/ExfYAWMymtrwUSWgEdujm7l3sAg9g1o1Q GE8mTgHj5rCl7r+8dFRBv/38ErjHT1r0iWAFf2C3BUrz9vHCv8S5dIa2LX1rzNLz Rt0vxuBqw8M0Ayx9lt1awg6nCpnBBYurDC/zXDrPbDdVCYfeU0BsWO/8tqtlbgT2 G9w84FoVxp7Z8VlIMCFlA2zs6SFz7JsDoeA3raAVGI/6ugLOpyypEBMs1OUIJqsi l2D4kF501KKaU73yqWjgom7C12yxow+ev+to51byrvLjKzg6CYG1a4XXvi3tPxq3 smPi9WIsgtRqAEFQ8TmDn5XpNpaYbg== -----END CERTIFICATE-----
- Domain Suffix Match should then also be uam.mesh-manager.com.
- Domain Name and/or RCOI LIST should match the config of the Hotspot2.0 AP.
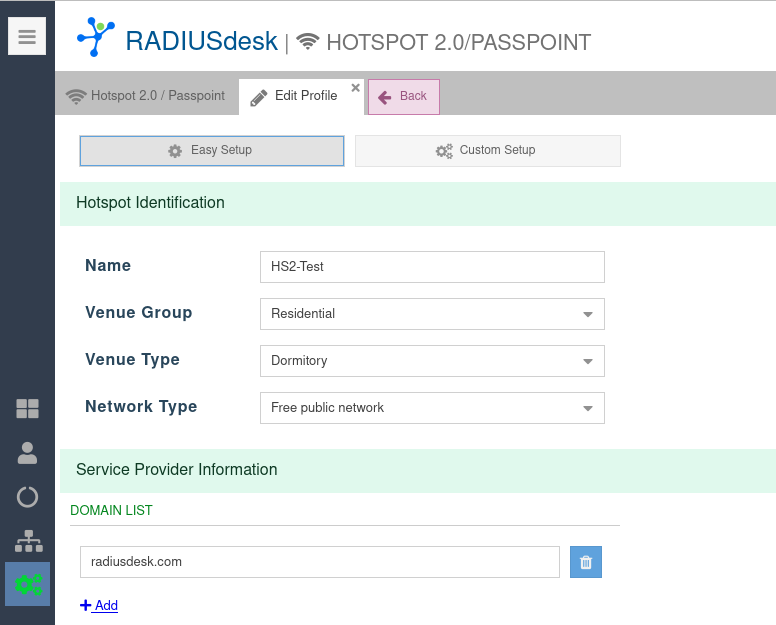
- See screenshot below where we set the Hotspot 2.0 Domain to radiusdesk.com on the Hotspot2.0/Passpoint profile.
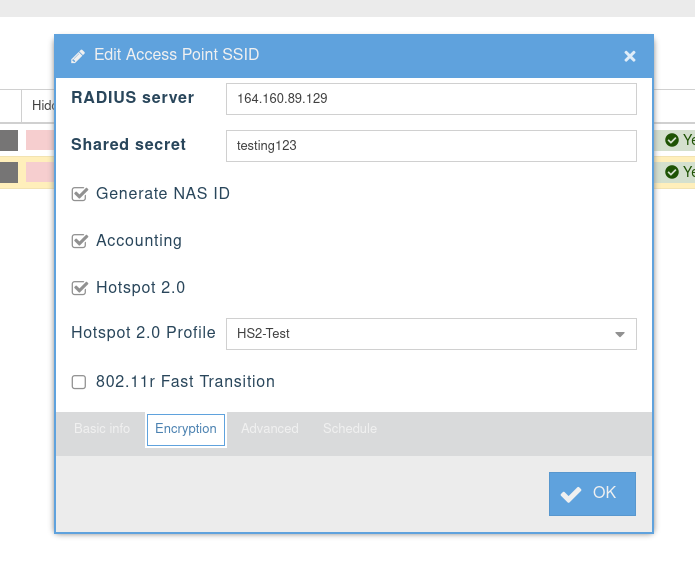
- We then choose an SSID in APdesk where we apply this Profile to:
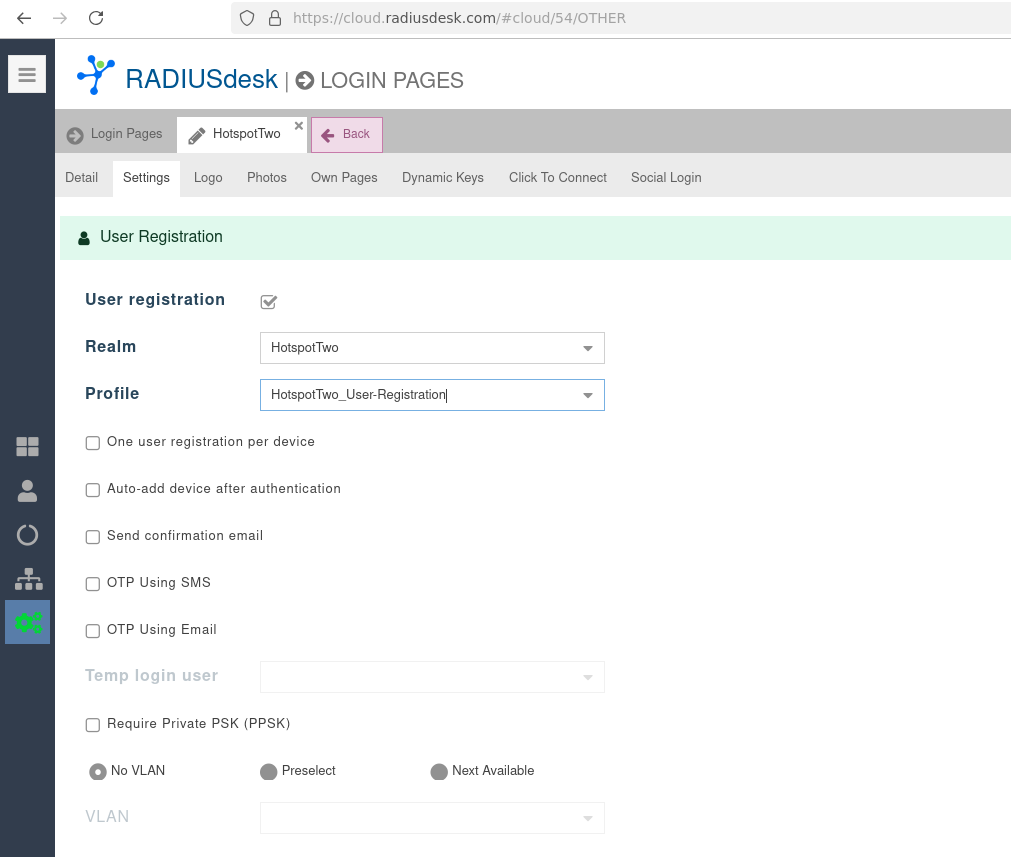
User Registration
- Select a Login Page in the same cloud as the Realm where you configured the Realm → Hotspot2.0/Passpoint settings.
- Enable User Registration.
- The last remaining item is to configure Rd-Connect.
Adjust Rd-Connect
- Refer to the file: /var/www/rd_connect/build/production/RdConnect/resources/js/config.js
window.AppConfig = { pageTitle : 'My ISP Portal', pageHeader : 'My ISP Portal', pageFooter : 'RADIUSdesk 2025', loginPageId : 50, i18n : 'en_GB' };
- Most items are self explanatory.
- The loginPageId should match the dynamic_id value when you preview the Login Page where you configured User Registration e.g. https://cloud.radiusdesk.com/login/bootstrap5/index.html?dynamic_id=50&i18n=en_GB
Rd-Connect Mobile App
- Everything is now in place for you to use Rd-Connect.
- Adjust the URL to match your RADIUSdesk server.
- You can also install the app on your phone as a PWA.
- See screenshots below.

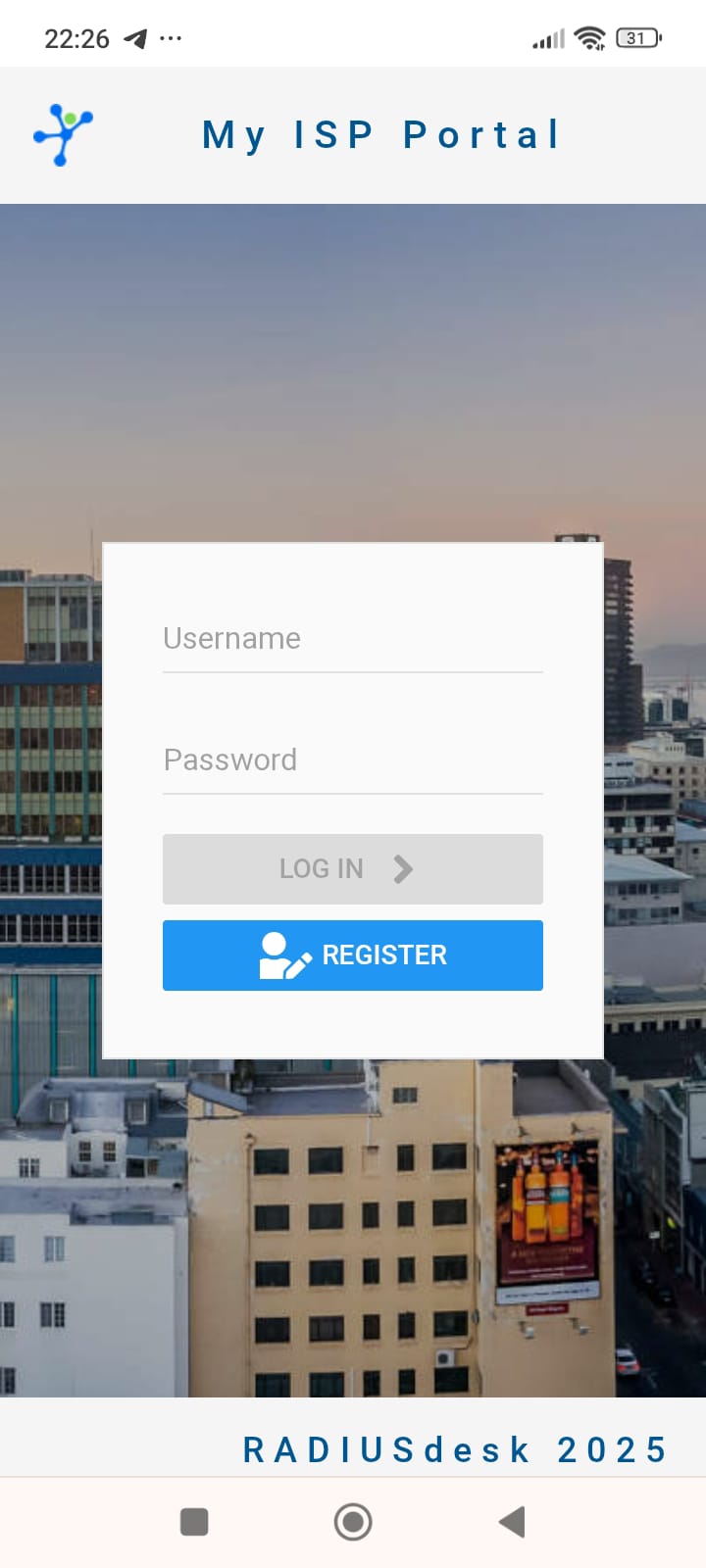
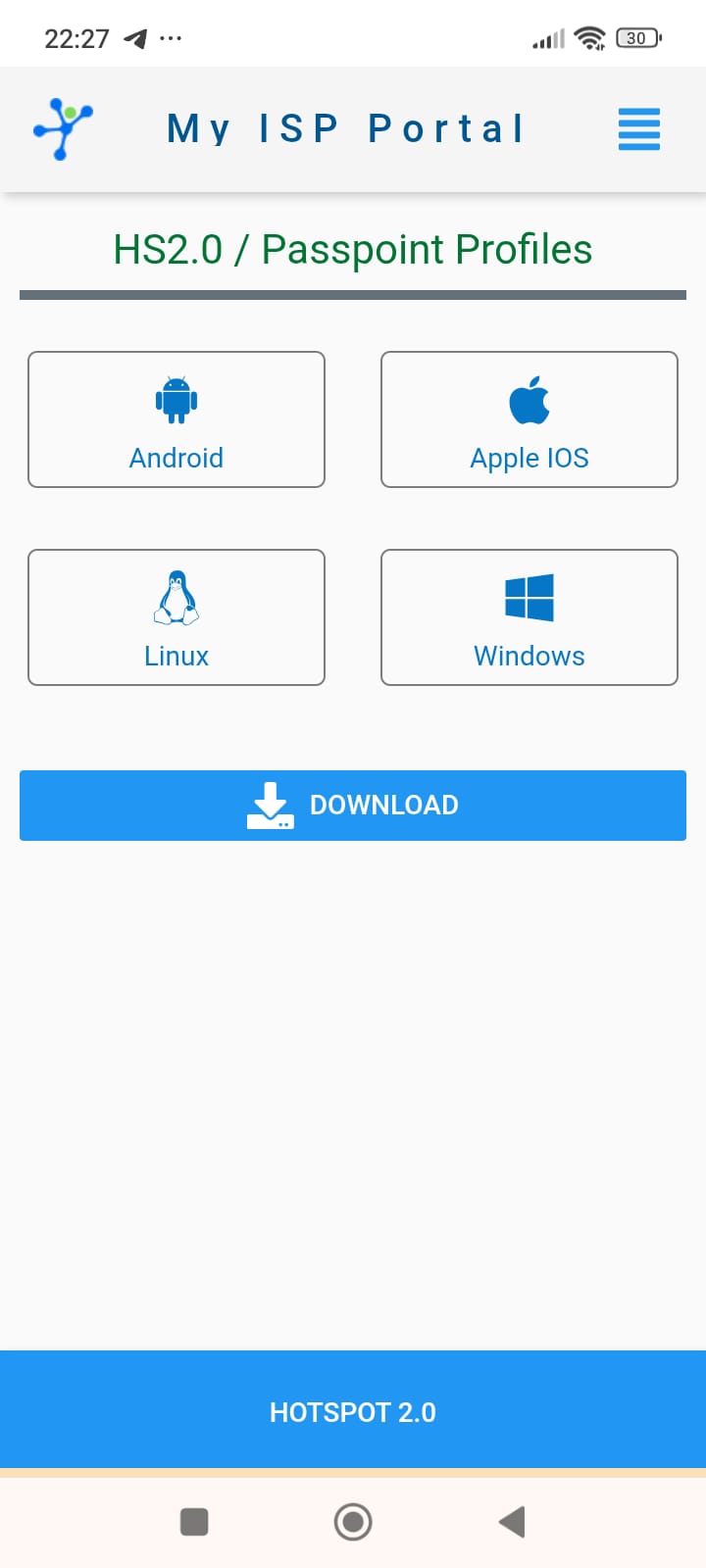
- After you logged in, you can download and install the Hotspot2.0/Passpoint profiles specific for your Operating System.
- In the next screenshot you can see where my phone used the downloaded and installed Hotspot2.0/Passpoint profile to connect to the Access Point that has Hotspot2.0/Passpoint configured.
- Note the Security is indicated as Passpoint.
- You will also see the name matches the name we specified under the Realm → Hotspot2.0/Passpoint settings (Wenley-HiFi-1.0.1).
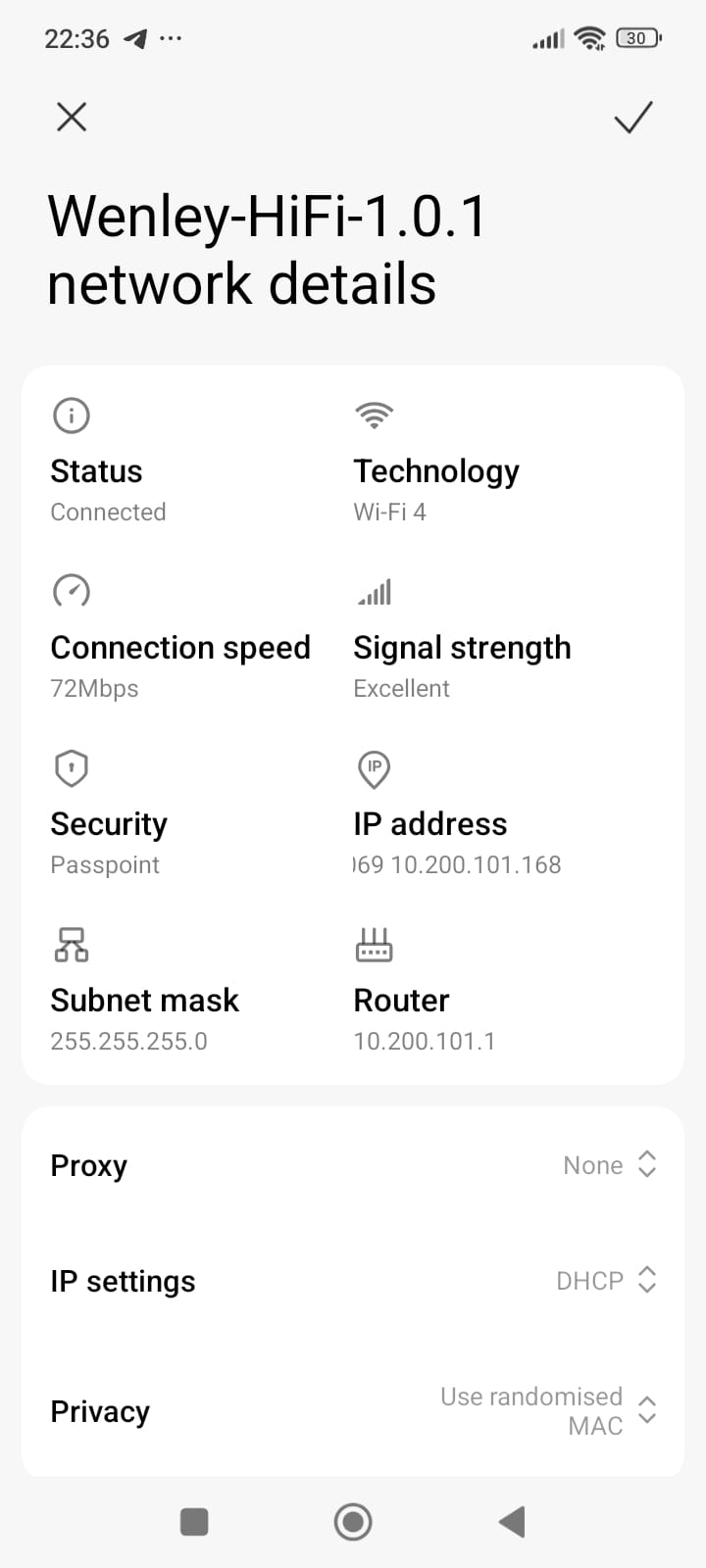
- As you can see from this page that Rd-Connect makes user registration and on-boarding on Hotspot2.0/Passpoint networks a snap.